Blog
sha256: 2b87a252a3d912530dd8c20df6bee7f6cbc4ede0074fdf217e318aab39d9736c
Medien Navigator
Medien Navigator
von NATO konform bis NATO kritisch, eine schoene Übersicht …
Any Comments ?
sha256: 8b7ae1266099eb7a85aaeeeabfbf37b4021d7d0fa37c28cb1a88d8aa9a298ddd
Hugo Forms PHP
Wanna add some simple forms and process the Content with PHP ?
Add RawHTML Template
if not yet done
mkdir layouts/shortcodes/
cat << 'EOF' > layouts/shortcodes/rawhtml.html
<!-- raw html -->
{{.Inner}}
EOF
Create Script
cat << 'EOF' > static/welcome.php
<html>
<body>
Welcome <?php echo $_POST["name"]; ?><br>
Your email address is: <?php echo $_POST["email"]; ?>
</body>
</html>
EOF
Create new Post and add rawhtml
without " " between { and {
hugo new content/post/rawtest.md
vim content/post/rawtest.md
{ {<rawhtml>} }
<form action="/welcome.php" method="post">
Name: <input type="text" name="name"><br>
E-mail: <input type="text" name="email"><br>
<input type="submit">
</form>
{ {</rawhtml>} }
Example
Just a small Form Example
HugoIO Templates
Custom Template Stuff
mkdir -p layouts/shortcodes
cat << 'EOF' > layouts/shortcodes/date.html
{{ now.Format "2006-01-02 03:04:05" }}
EOF
Insert Code in Template
current date ? { {< date >} }
Result ?
current date ?? 2026-01-15 03:36:13
Add RawHTML
Create Template
cat << 'EOF' > layouts/shortcodes/rawhtml.html
<!-- raw html -->
{{.Inner}}
EOF
Add Code
{ {< rawhtml >} }
<p class="speshal-fancy-custom">
This is <strong>raw HTML</strong>, inside Markdown.
</p>
{ {< /rawhtml >} }
Result ?
This is raw HTML, inside Markdown.
OpenBSD with IPSEC -> GIF -> OSFP
Intro
Stage two Machines, puffy206 and puffy207 Both Maschines needs static IP Adresses
puffy206
Loopback & Gif
doas su -
cat << 'EOF' > /etc/hostname.lo1
inet 10.0.0.6/32
up
EOF
cat << 'EOF' > /etc/hostname.gif0
description "Point2Point Interface for OSPF"
mtu 1420
10.10.10.6 10.10.10.7 netmask 255.255.255.255
tunnel 192.168.108.206 192.168.108.207
EOF
Enable IPSEC & IP Forwarding
cat << 'EOF' >> /etc/sysctl.conf
net.inet.ip.forwarding=1
net.inet.gre.allow=1
EOF
rcctl enable ipsec isakmpd
rcctl set isakmpd flags -K
Create Tunnel Endpoint
cat << 'EOF' > /etc/ipsec.conf
ike active esp transport from 192.168.108.206 to 192.168.108.207 peer 192.168.108.207 \
main auth "hmac-sha2-256" enc "aes-128" group modp3072 \
quick enc "aes-128-gcm" group modp3072 \
srcid 192.168.108.206 \
psk "my-tunnel-is-private"
EOF
chmod 600 /etc/ipsec.conf
Create ospfd.conf
cat << 'EOF' > /etc/ospfd.conf
# macros
id="192.168.108.206"
# global configuration
router-id id
fib-update yes
stub router yes
spf-delay 1
spf-holdtime 5
# areas
area 0.0.0.0 {
interface gif0
interface lo1 {}
}
EOF
chmod 600 /etc/ospfd.conf
rcctl enable ospfd
Reboot and Check
reboot
gnuwatch "ipsecctl -s all"
puffy207
Loopback & Gif
doas su -
cat << 'EOF' > /etc/hostname.lo1
inet 10.0.0.7/32
up
EOF
cat << 'EOF' > /etc/hostname.gif0
description "Point2Point Interface for OSPF"
mtu 1420
10.10.10.7 10.10.10.6 netmask 255.255.255.255
tunnel 192.168.108.207 192.168.108.206
EOF
Enable IPSEC & IP Forwarding
cat << 'EOF' >> /etc/sysctl.conf
net.inet.ip.forwarding=1
net.inet.gre.allow=1
EOF
rcctl enable ipsec isakmpd
rcctl set isakmpd flags -K
Create Tunnel Endpoint
cat << 'EOF' > /etc/ipsec.conf
ike active esp transport from 192.168.108.207 to 192.168.108.206 peer 192.168.108.206 \
main auth "hmac-sha2-256" enc "aes-128" group modp3072 \
quick enc "aes-128-gcm" group modp3072 \
srcid 192.168.108.207 \
psk "my-tunnel-is-private"
EOF
chmod 600 /etc/ipsec.conf
Create ospfd.conf
cat << 'EOF' > /etc/ospfd.conf
# macros
id="192.168.108.207"
# global configuration
router-id $id
fib-update yes
stub router yes
spf-delay 1
spf-holdtime 5
# areas
area 0.0.0.0 {
interface gif0
interface lo1 {}
}
EOF
chmod 600 /etc/ospfd.conf
rcctl enable ospfd
Reboot and Check
reboot
gnuwatch "ipsecctl -s all"
Test
ifconfig gif
ipsecctl -s all
route -n show -inet
ospfctl show nei
Throughput Test
root@client2 ~# tcpbench 10.0.0.7
elapsed_ms bytes mbps bwidth
1000 2801664 22.413 100.00%
Conn: 1 Mbps: 22.413 Peak Mbps: 22.413 Avg Mbps: 22.413
2009 2775672 22.007 100.00%
Conn: 1 Mbps: 22.007 Peak Mbps: 22.413 Avg Mbps: 22.007
3014 3173760 25.264 100.00%
Conn: 1 Mbps: 25.264 Peak Mbps: 25.264 Avg Mbps: 25.264
4021 3192912 25.391 100.00%
Conn: 1 Mbps: 25.391 Peak Mbps: 25.391 Avg Mbps: 25.391
Any Comments ?
sha256: d27ad9e5808a63352b5e5070af2abd82a9924129b713f98d1d10d4f8a8085df4
IPSEC with OpenBSD
Intro
Stage a few Machines, puffy206 - 209 puffy206 has got a static ip, while puffy207 - 209 got dynamic ip addresses
Master, puffy206
Loopback
doas su -
cat << 'EOF' > /etc/hostname.lo1
inet 10.0.0.6/32
up
EOF
Enable IPSEC & IP Forwarding
cat << 'EOF' >> /etc/sysctl.conf
net.inet.ip.forwarding=1
net.inet.gre.allow=1
EOF
rcctl enable ipsec isakmpd
rcctl set isakmpd flags -K
Create Tunnel Endpoint
cat << 'EOF' > /etc/ipsec.conf
ike dynamic esp tunnel from 10.0.0.6/32 to 10.0.0.7/32 peer any \
main group "modp1024" quick group "modp1024" \
psk "my-tunnel-is-private"
ike dynamic esp tunnel from 10.0.0.6/32 to 10.0.0.8/32 peer any \
main group "modp1024" quick group "modp1024" \
psk "my-tunnel-is-private"
ike dynamic esp tunnel from 10.0.0.6/32 to 10.0.0.8/32 peer any \
main group "modp1024" quick group "modp1024" \
psk "my-tunnel-is-private"
EOF
chmod 600 /etc/ipsec.conf
Reboot and Check
reboot
gnuwatch "ipsecctl -s all"
Slave, puffy207
Loopback
doas su -
cat << 'EOF' > /etc/hostname.lo1
inet 10.0.0.7/32
up
EOF
Enable IPSEC & IP Forwarding
cat << 'EOF' >> /etc/sysctl.conf
net.inet.ip.forwarding=1
net.inet.gre.allow=1
EOF
rcctl enable ipsec isakmpd
rcctl set isakmpd flags -K
IPSEC
cat << 'EOF' > /etc/ipsec.conf
ike esp tunnel from 10.0.0.7/32 to 10.0.0.6/32 peer 192.168.108.206 \
main group "modp1024" quick group "modp1024" \
psk "my-tunnel-is-private"
EOF
chmod 600 /etc/ipsec.conf
Slave, puffy208
Loopback
doas su -
cat << 'EOF' > /etc/hostname.lo1
inet 10.0.0.8/32
up
EOF
Enable IPSEC & IP Forwarding
cat << 'EOF' >> /etc/sysctl.conf
net.inet.ip.forwarding=1
net.inet.gre.allow=1
EOF
rcctl enable ipsec isakmpd
rcctl set isakmpd flags -K
IPSEC
cat << 'EOF' > /etc/ipsec.conf
ike esp tunnel from 10.0.0.8/32 to 10.0.0.6/32 peer 192.168.108.206 \
main group "modp1024" quick group "modp1024" \
psk "my-tunnel-is-private"
EOF
chmod 600 /etc/ipsec.conf
Slave, puffy209
Loopback
doas su -
cat << 'EOF' > /etc/hostname.lo1
inet 10.0.0.9/32
up
EOF
Enable IPSEC & IP Forwarding
cat << 'EOF' >> /etc/sysctl.conf
net.inet.ip.forwarding=1
net.inet.gre.allow=1
EOF
rcctl enable ipsec isakmpd
rcctl set isakmpd flags -K
IPSEC
cat << 'EOF' > /etc/ipsec.conf
ike esp tunnel from 10.0.0.9/32 to 10.0.0.6/32 peer 192.168.108.206 \
main group "modp1024" quick group "modp1024" \
psk "my-tunnel-is-private"
EOF
chmod 600 /etc/ipsec.conf
Full IPSEC Example
cat /etc/ipsec.conf
#
# https://man.openbsd.org/ipsec.conf.5
# http://www.kernel-panic.it/openbsd/vpn/vpn3.html
# https://www.packetmischief.ca/openbsd-ipsec-tunnel-guide/
#
# ike [mode] [encap] [tmode] [proto protocol] \
# from src [port sport] [(srcnat)] to dst [port dport] \
# [local localip] [peer remote] \
# [mode auth algorithm enc algorithm group group] \
# [quick auth algorithm enc algorithm group group] \
# [srcid string] [dstid string] \
# [psk string] [tag string]
# mode: active (default), passive, dynamic
# encap: esp (default), ah
# tmode: tunnel (default), transport
# mode: main (default), aggressive -> this is phase 1
# quick: -> this is phase 2
# Var
local_gw = "MEINE-PUBLIC-IP"
local_net = "MEIN-NETZWERK/MASK"
auth1 = "hmac-sha1" # hmac-sha1, hmac-sha2-256, hmac-sha2-384, hmac-sha2-512
enc1 = "aes-128" # aes-128 (=aes), aes-192, aes-256, blowfish
group1 = "modp3072" # modp768 (g1), modp1024 (g2), modp1536 (g5), modp2048 (g14), modp3072 (g15), modp4096 (g16), modp6144 (g17), modp8192 (g18), ... (g30)
time1 = "3600" # in Seconds, or 10m, resp 12h
auth2 = "hmac-sha2-256" # siehe oben
enc2 = "aes-128" # siehe oben
group2 = "modp3072" # siehe oben
time2 = "1200" # siehe oben
# Tunnel to Remote
remote_gw = "DEINE-PUBLIC-IP"
remote_net = "DEIN-NETZWERK/MASK"
key = "super-huper-secret-key""
ike dynamic esp tunnel from $local_net to $remote_net peer $remote_gw \
main auth $auth1 enc $enc1 group $group1 lifetime $time1 \
quick auth $auth2 enc $enc2 group $group2 lifetime $time2 \
srcid $local_gw \
psk $key
ike dynamic esp tunnel from $remote_net to $local_net peer $remote_gw \
main auth $auth1 enc $enc1 group $group1 lifetime $time1 \
quick auth $auth2 enc $enc2 group $group2 lifetime $time2 \
srcid $local_gw \
psk $key
Links
Tweak Nginx Webserver with limited Client Certificate
Install NGINX & PHP
pkg_add nginx php--%7.3
rcctl enable nginx php73_fpm
Edit php.ini
sed -i s'/date.timezone = UTC.*/date.timezone = Europe\/Zurich/' /etc/php-7.3.ini
sed -i s'/short_open_tag = Off.*/short_open_tag = On/' /etc/php-7.3.ini
nginx.conf
mkdir /var/log/nginx
cat << 'EOF' > /etc/nginx/nginx.conf
worker_processes 1;
worker_rlimit_nofile 1024;
events {
worker_connections 800;
}
http {
include mime.types;
default_type application/octet-stream;
index index.php index.html index.htm;
keepalive_timeout 65;
server_tokens off;
proxy_cache_valid any 0s;
log_format main '$remote_addr - $ssl_client_serial - [$time_local] - "$request" - $status - $body_bytes_sent';
map $ssl_client_serial $ssl_access {
default 0;
WFuDgzQBZXV740D3 1; # Hans Muster
EDugUslEX1Et90WX 0; # Beat Breu
2DF3C663741296F5 1; # Ruedi Ruessel
}
#
# HTTP -> Redirect to HTTPS
#
server {
listen 80;
server_name localhost;
access_log logs/host.access.log main;
return 301 https://$host$request_uri;
}
#
# HTTPS server
#
server {
listen 443 ssl;
server_name localhost;
access_log /var/log/nginx/puffy205.log main;
error_log /var/log/nginx/puffy205-error.log;
ssl_certificate /etc/ssl/combo/host.crt;
ssl_certificate_key /etc/ssl/combo/host.crt;
ssl_session_timeout 5m;
ssl_session_cache shared:SSL:1m;
ssl_ciphers HIGH:!aNULL:!MD5:!RC4;
ssl_prefer_server_ciphers on;
ssl_client_certificate /etc/ssl/combo/root.crt;
ssl_verify_client optional;
root /var/www/htdocs;
location / {
# Block if no Cert
if ($ssl_client_verify != SUCCESS) {
return 403;
}
# Block if not whitelisted
if ($ssl_access = 0) {
return 403;
}
}
location ~ \.php$ {
try_files $uri $uri/ =404;
fastcgi_pass unix:run/php-fpm.sock;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_param SSL_CLIENT_SERIAL $ssl_client_serial;
include fastcgi_params;
}
}
}
EOF
Root Cert, Server Cert
mkdir -p /etc/ssl/combo/
cat << 'EOF' > /etc/ssl/combo/host.crt
-----BEGIN CERTIFICATE-----
MIID6jCCAtKgAwIBAgIIaGXwEvomrIYwDQYJKoZIhvcNAQELBQAwWjELMAkGA1UE
BhMCQ0gxFDASBgNVBAgTC1N3aXR6ZXJsYW5kMQ8wDQYDVQQHEwZadXJpY2gxEjAQ
BgNVBAoTCVN0b2VnZSBBRzEQMA4GA1UEAxMHcm9vdCBDQTAeFw0yMDA0MDIxNTE1
MDBaFw0yMjA2MTExNTE1MDBaMGIxCzAJBgNVBAYTAkNIMRQwEgYDVQQIEwtTd2l0
emVybGFuZDEPMA0GA1UEBxMGWnVyaWNoMRIwEAYDVQQKEwlTdG9lZ2UgQUcxGDAW
BgNVBAMTD3B1ZmZ5MjA1LnBsYW5ldDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCC
AQoCggEBAKiWF3qZvvXDPxuwhMHE3WDIQIJvRPKmBQQsEnnn598tD+W7aeSgvnZ3
Oel3n4WRl6syNF3CLPo3EbMy8VgZrCOul8Uvjro9WLZeL7tG5CndRFZu9Erzq2Ic
KodQGxEc3jC3UxFypr4OuUAigrlWi5dRp3dhzP4/xqQ42c1axPoI/YDzIdw5O6WZ
QWZf0YfsAIbbkw3YymLBoZQxyBmhasaU6xBnIAMLuYA6IVqz3QoGHxDr8bij34y5
TRb0575TzTdAtmWhN3GE+xGOJ/KPQ6MZjaA9oz15bMVuVg1uZgUXE5K22kx6eZLk
ejhV4nxnokftPJBZfaC9LbX661B9GTUCAwEAAaOBqzCBqDAMBgNVHRMBAf8EAjAA
MB0GA1UdDgQWBBT9D1+1pNUT3SuAfeptzaeszgUivTALBgNVHQ8EBAMCBeAwEwYD
VR0lBAwwCgYIKwYBBQUHAwEwJAYDVR0RBB0wG4IPcHVmZnkyMDUucGxhbmV0gghw
dWZmeTIwNTARBglghkgBhvhCAQEEBAMCBkAwHgYJYIZIAYb4QgENBBEWD3hjYSBj
ZXJ0aWZpY2F0ZTANBgkqhkiG9w0BAQsFAAOCAQEAKfRir/cZkKdeoDWV5qN3NNw/
AWNJZjkA6KvFwuXjvMR00/vlaqTuOOBKEU5CtxnHDKhfpkjSnX7ynoJXoAQYkNag
3reSKkFZ1TX1yz/Pf/f8YLbiA3e1hx9E0E5gAENtYB6vkZh5quhRnqsHSJpJP6H6
IYaZLh7w4+RL5qvQmN1tlyKwInrJmY6jsLPhALUDFQewDPJDla/iJ6ivlHsvCtMC
MA/slsJ2iWaHbAIzCXZyBeJHR949zJvja0jJPJHVDknsKypO9WEeMclaSoY1AfVI
dGg5W8ahwxuwX2e3ygbORoG0R1Qoeqdp8+VRvOpxM4R97NPtkEq/XPgrtWnoyQ==
-----END CERTIFICATE-----
-----BEGIN RSA PRIVATE KEY-----
MIIEpQIBAAKCAQEAqJYXepm+9cM/G7CEwcTdYMhAgm9E8qYFBCwSeefn3y0P5btp
...
AsoXCZvnbPzWsP8M2JokEngD0201NZN8/aBuDi0+aF1b3xA1vtKumdM=
-----END RSA PRIVATE KEY-----
EOF
chmod 440 /etc/ssl/combo/host.crt
cat << 'EOF' > /etc/ssl/combo/root.crt
-----BEGIN CERTIFICATE-----
MIIDqDCCApCgAwIBAgIIe1F3tBzaragwDQYJKoZIhvcNAQEMBQAwWjELMAkGA1UE
BhMCQ0gxFDASBgNVBAgTC1N3aXR6ZXJsYW5kMQ8wDQYDVQQHEwZadXJpY2gxEjAQ
BgNVBAoTCVN0b2VnZSBBRzEQMA4GA1UEAxMHcm9vdCBDQTAeFw0xOTA2MDUyMDA0
MDBaFw0yOTA2MDUyMDA0MDBaMFoxCzAJBgNVBAYTAkNIMRQwEgYDVQQIEwtTd2l0
emVybGFuZDEPMA0GA1UEBxMGWnVyaWNoMRIwEAYDVQQKEwlTdG9lZ2UgQUcxEDAO
BgNVBAMTB3Jvb3QgQ0EwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC8
kBixlR0b3tE7Db6CuFTYeKdSGbnLx2Df8zir0ueFlv6JX5rLgbWbb5rMnWOH1O1N
AmCbuh0CrXD1evl1Glyf3hmumIvW4GVfWcQNvBsq1iUfoJn24qGnTu502xX1Gv5F
TCOxq2HqdLEwsktl2Pn76/49quj1PlBSSpYLWBsvqj1NkNIXgMzUjBURF+fEtRby
SE5RLbw+fubAw1e9K3Xu5VLgItno3g9t2B4MKTApsCZsOR288kedrAUxFhyB2pD/
6L9sbyM1h5r+EMjAzyeTeUKtXXqC+AyLthkw3eB58UY/QxpoNiggQY+5yd57yzxK
Ox1QHh+kj2+8eK5b3+pFAgMBAAGjcjBwMA8GA1UdEwEB/wQFMAMBAf8wHQYDVR0O
BBYEFG8FFqfTRx/lTT0qfF/tEknHS7LSMAsGA1UdDwQEAwIBBjARBglghkgBhvhC
AQEEBAMCAAcwHgYJYIZIAYb4QgENBBEWD3hjYSBjZXJ0aWZpY2F0ZTANBgkqhkiG
9w0BAQwFAAOCAQEATzFY8H0EX+yFWEgRtGNciIp0WsQ53cjRnNxdkDsW+W2gB+cs
QdS2LBoWts5jLHXrZstJAoy1qyEhqyYvXFMf4SsfKsrXfli7fgod5figyVjhmz41
6v/Ss668kyjWOYkY3CYqPTJolxDuIpMIq/AMGurlcf6oTDdP/FPs4nvdGed16Qjp
849n7r+ugQKrbDC4VpDXcZECXlQjI3QgUeXKqly0LXcwqFXqC3+m1O6YTwyIFrLy
8ZyWjAKN4NdKd88eiczvEj3uQVXhqkbmiEyp3q5jsXcQLzblJ0aCABqppvGLgASq
Z9QeBLjqhJ3DIcgKcHqJsox+xKrDLtIvgYmaOg==
-----END CERTIFICATE-----
EOF
chmod 440 /etc/ssl/combo/root.crt
index.php
cat << 'EOF' > /var/www/htdocs/index.php
Hi <?
$array = [
"WFuDgzQBZXV740D3" => "Hans Muster",
"EDugUslEX1Et90WX" => "Beat Breu",
"2DF3C663741296F5" => "Ruedi Ruessel"
];
echo $array[$_SERVER['SSL_CLIENT_SERIAL']];
?>, your Certificat Serial Number is
<?
echo $_SERVER['SSL_CLIENT_SERIAL'];
?>
EOF
Start all stuff
rcctl restart nginx php73_fpm
Open Webpage:
Keepalive
Little Keep Alive
… mit freundlicher genehmigung von Kumpel Marc :)
keepalive.sh
#!/usr/bin/env bash
FILE="$HOME/scripts/excuses"
# Linux or BSD ? nf points to the right binary
which numfmt > /dev/null 2>&1 && nf=$(which numfmt) || nf=$(which gnumfmt);
# Linux or BSD ? gs points to the right binary
which shuf > /dev/null 2>&1 && gs=$(which shuf) || gs=$(which gshuf);
if [ ! -e "$FILE" ]; then
echo ""
echo "$FILE does not exist"
echo "##############################################"
command -v curl >/dev/null 2>&1 || { echo >&2 "Holy cow! You don't even have curl, get lost!"; echo ""; exit 1; }
mkdir -p $HOME/scripts/
curl -o $FILE https://pages.cs.wisc.edu/~ballard/bofh/excuses
echo "##############################################"
fi
keep () {
clear;
echo "If you are reading this..." && echo "Congratulations, you are alive."
echo ""
echo "You are stuck on the following planet:" `hostname`
echo "It has been" `date +%s | $nf --g` "seconds since January 1st 1970, this is quite a while..."
echo ""; echo "Your current excuse is:"; $gs -n 1 $HOME/scripts/excuses
}
while :
do
keep
sleep 30
done
Testrun
./keepalive.sh
If you are reading this...
Congratulations, you are alive.
You are stuck on the following planet: puffy201.planet
It has been 1658870361 seconds since January 1st 1970, this is quite a while...
Your current excuse is:
Power Company having EMP problems with their reactor
Any Comments ?
sha256: 5de0afbcacd56dbcaede593a6f243a3f46e4d94754683646d57e00f3c7840eca
Librenms on Debian 10.3
How to Install LibreNMS on Debian
https://docs.librenms.org/Installation/Installation-Ubuntu-1804-Apache/
Packages
apt-get install acl apache2 borgbackup curl fping hping3 htop ipcalc jq lftp lynx mlocate mtr nmap pwgen rsync sipcalc tmate tree tshark unzip vim vnstat wget zip curl apache2 composer fping git graphviz imagemagick python-memcache python-mysqldb rrdtool snmp snmpd whois mariadb-client mariadb-server mtr-tiny nmap libapache2-mod-php7.3
apt-get install php7.3-cli php7.3-curl php7.3-gd php7.3-json php7.3-mbstring php7.3-mysql php7.3-snmp php7.3-xml php7.3-zip
add User
useradd librenms -d /opt/librenms -M -r
usermod -a -G librenms www-data
get Git
cd /opt
git clone https://github.com/librenms/librenms.git
set Permission
chown -R librenms:librenms /opt/librenms
chmod 770 /opt/librenms
setfacl -d -m g::rwx /opt/librenms/rrd /opt/librenms/logs /opt/librenms/bootstrap/cache/ /opt/librenms/storage/
setfacl -R -m g::rwx /opt/librenms/rrd /opt/librenms/logs /opt/librenms/bootstrap/cache/ /opt/librenms/storage/
add Dependencis
su - librenms
./scripts/composer_wrapper.php install --no-dev
exit
Configure MySQL
systemctl restart mysql
mysql -uroot -p
CREATE DATABASE librenms CHARACTER SET utf8 COLLATE utf8_unicode_ci;
CREATE USER 'librenms'@'localhost' IDENTIFIED BY 'password';
GRANT ALL PRIVILEGES ON librenms.* TO 'librenms'@'localhost';
FLUSH PRIVILEGES;
exit
MySQL Conf
vi /etc/mysql/mariadb.conf.d/50-server.cnf
Within the [mysqld] section please add:
innodb_file_per_table=1
lower_case_table_names=0
systemctl restart mysql
PHP Ini
vi /etc/php/7.3/apache2/php.ini
[Date]
date.timezone = Europe/Zurich
vi /etc/php/7.3/cli/php.ini
[Date]
date.timezone = Europe/Zurich
Update Apache
a2enmod php7.3
a2dismod mpm_event
a2enmod mpm_prefork
Configure Apache
cat << EOF > /etc/apache2/sites-available/librenms.conf
<VirtualHost *:80>
DocumentRoot /opt/librenms/html/
ServerName host211.planet
AllowEncodedSlashes NoDecode
<Directory "/opt/librenms/html/">
Require all granted
AllowOverride All
Options FollowSymLinks MultiViews
</Directory>
</VirtualHost>
EOF
Enable Site librenms.conf
a2ensite librenms.conf
a2enmod rewrite
systemctl restart apache2
SNMP
cp /opt/librenms/snmpd.conf.example /etc/snmp/snmpd.conf
vi /etc/snmp/snmpd.conf
curl -o /usr/bin/distro https://raw.githubusercontent.com/librenms/librenms-agent/master/snmp/distro
chmod +x /usr/bin/distro
systemctl restart snmpd
Crontab
cp /opt/librenms/librenms.nonroot.cron /etc/cron.d/librenms
Logrotate
cp /opt/librenms/misc/librenms.logrotate /etc/logrotate.d/librenms
Configure Web
http://host211.planet/install.php
Fix Permission
chown librenms:librenms /opt/librenms/config.php
Any Comments ?
sha256: 9f39db52f8279c0fbb2f3072bc1da003c2334bb210d5aef9a3878e7ff55fbd13
Smokeping on Debian 10.3
How to install Smokeping on Debian in 5 Minutes
Installer …
wget https://blog.stoege.net/scripts/smokeping_debian.sh
Set Hostname
root@smokeping:~# cat /etc/hostname
smokeping.planet
Install Packages
apt-get install apache2 borgbackup curl echoping fping hping3 htop ipcalc jq lftp lynx mlocate mtr nmap pwgen rsync sipcalc smokeping tmate tree tshark unzip vim vnstat wget zip
Enable Smokeping in Apache
cd /etc/apache2/conf-enabled
ln -s ../conf-available/smokeping.conf .
Enable Module CGI
a2enmod cgid
systemctl restart apache2
Some Smokeping Fixes
mkdir -p /var/run/smokeping
Tune General
cat << 'EOF' > /etc/smokeping/config.d/General
*** General ***
owner = Franz Musterer
contact = nospam@nomail.ch
mailhost = smtp-relay-host
# NOTE: do not put the Image Cache below cgi-bin
# since all files under cgi-bin will be executed ... this is not
# good for images.
cgiurl = http://host211/smokeping/smokeping.cgi
# specify this to get syslog logging
syslogfacility = local0
# each probe is now run in its own process
# disable this to revert to the old behaviour
# concurrentprobes = no
@include /etc/smokeping/config.d/pathnames
EOF
Tune Databases
cat << 'EOF' > /etc/smokeping/config.d/Database
*** Database ***
step = 300
pings = 20
#step = 60
#pings = 59
# consfn mrhb steps total
AVERAGE 0.5 1 1008
AVERAGE 0.5 12 4320
MIN 0.5 12 4320
MAX 0.5 12 4320
AVERAGE 0.5 144 720
MAX 0.5 144 720
MIN 0.5 144 720
EOF
Tune Probes
cat << EOF > /etc/smokeping/config.d/Probes
*** Probes ***
+ FPing
binary = /usr/bin/fping
+ EchoPingHttp
binary = /usr/bin/echoping
forks = 5
offset = 50%
step = 300
# The following variables can be overridden in each target section
accept_redirects = yes
extraopts =
ignore_cache = yes
ipversion = 4
pings = 5
port = 80
priority = 6
revalidate_data = no
timeout = 20
tos = 0xa0
url = /
waittime = 1
+EchoPingHttps
binary = /usr/bin/echoping
forks = 5
offset = 50%
step = 300
# The following variables can be overridden in each target section
accept_redirects = yes
extraopts =
ignore_cache = yes
ipversion = 4
pings = 5
port = 443
priority = 6
prot = 3443
revalidate_data = no
timeout = 20
tos = 0xa0
url = /
waittime = 1
+EchoPingDNS
binary = /usr/bin/echoping
forks = 5
offset = 50%
step = 300
# The following variables can be overridden in each target section
dns_request = google.com
dns_tcp = no
dns_type = A
extraopts =
ipversion = 4
pings = 5
plugin = /usr/lib/echoping/dns.so
pluginargs = -p
priority = 6
timeout = 1
tos = 0xa0
waittime = 1
EOF
Tune Targets
cat << 'EOF' > /etc/smokeping/config.d/Targets
*** Targets ***
probe = FPing
menu = Top
title = Network Latency Grapher
remark = Welcome to the SmokePing website of xxx Company. \
Here you will learn all about the latency of our network.
+ Local
menu = Local
title = Local Network
++ LocalMachine
menu = Local Machine
title = This host
host = localhost
+ Planet
menu = Planet
title = My Little Planet
++ host1
host = host1.planet
++ host2
host = host2.planet
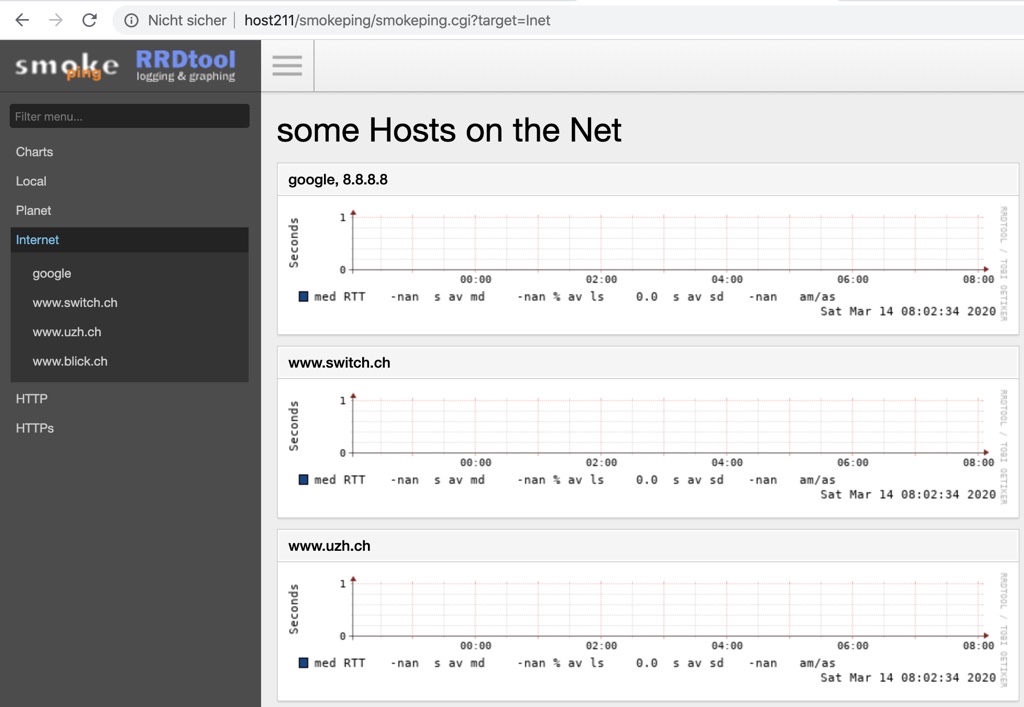
+ Inet
menu = Internet
title = some Hosts on the Net
++ google
menu = google
title = google, 8.8.8.8
host = 8.8.8.8
++ switch
host = www.switch.ch
++ uzh
host = www.uzh.ch
++ blick
host = www.blick.ch
+ HTTP
menu = HTTP
title = some HTTP Probes
probe = EchoPingHttp
++ example-net
host = www.example.net
++ example-ch
host = www.example.ch
++ example-com
host = www.example.com
EOF
Restart Smokeping
systemctl restart smokeping
Browse
http://IP-OF-HOST/smokeping