Slides - SSH Agent
made a few Slides about SSH Agent & Agent Forwarding with https://slides.com. Do you like it ? I do …
Any Comments ?
sha256: dd15fd6475246beedee7f6c61924134c76248cf5e28d7092283475c97e9f2f50
made a few Slides about SSH Agent & Agent Forwarding with https://slides.com. Do you like it ? I do …
sha256: dd15fd6475246beedee7f6c61924134c76248cf5e28d7092283475c97e9f2f50
Inspired by a book from MWL - OpenBSD Mastery Filesystems, here some Notes ..
build a RAID with 3 Disks, add some Data, destroy one Disk, and rebuild the Raid (and it’s Data).
root@puffy # dmesg |grep -i sec
wd0: 64-sector PIO, LBA, 20480MB, 41943040 sectors
sd0: 20480MB, 512 bytes/sector, 41943040 sectors
sd1: 20480MB, 512 bytes/sector, 41943040 sectors
sd2: 20480MB, 512 bytes/sector, 41943040 sectors
sd0, sd1, sd2 are New Disks for RAID
If you need multiple SSH keys with passphrases for educational purposes, you can generate them as follows. The passphrase is set in the comments of the corresponding public key.
cat << 'EOF' > /tmp/ssh-key-generator.sh
#!/usr/bin/env bash
# File
f=/tmp/id_ed25519
# Cleanup
test -f $f && rm $f $f.pub
# Gen Key
ssh-keygen -o -a 100 -t ed25519 -N "" -f ${f}
# Extact Password (last 8 Char from PubKey)
pw=$(cat ${f}.pub |cut -d" " -f 2 |gsed -E 's/^.{60}//')
pw2=$(echo $pw |gsed -E 's/\//x/g')
id=$(echo $pw2 |gsed -E 's/^....//')
# Rename
mv ${f} ${f}-${id}
mv ${f}.pub ${f}-${id}.pub
# Set Var
x="${f}-${id}"
f="$x"
# Prepare Password
cat << EOF2 > ${f}.x
#!/bin/sh
echo $pw2
EOF2
chmod +x ${f}.x
# Set Comment
ssh-keygen -c -C "Password: $pw2" -f ${f}
# Set Password
ssh-keygen -p -N "$pw2" -f ${f}
# Show Key
cat ${f}.pub
# Add to Agent
DISPLAY=1 SSH_ASKPASS="${f}.x" ssh-add ${f} < /dev/null
# Cleanup
rm ${f}.x
exit 0
EOF
cd /tmp
chmod +x /tmp/ssh-key-generator.sh
./ssh-key-generator.sh; ls -la /tmp/id*
user@host /tmp$ ./ssh-key-generator.sh; ls -la id_ed25519-*
Generating public/private ed25519 key pair.
Your identification has been saved in /tmp/id_ed25519
Your public key has been saved in /tmp/id_ed25519.pub
The key fingerprint is:
SHA256:IdJGeVPDOMrk9BidtIKrIzFBn8vNgjHVT8/sdSA9hik user@host
The key's randomart image is:
+--[ED25519 256]--+
| . .. .+.=* |
|. o .==EB=.* |
|.o oo=B*Boo o |
| .= ++=+.= . . |
|o. +.o S . . |
| o .. . |
|. o |
| . . |
| |
+----[SHA256]-----+
Old comment: user@host
Comment 'Password: S4seK144' applied
Key has comment 'Password: S4seK144'
Your identification has been saved with the new passphrase.
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMKxvcjpd8DvAfdO0nZ34uCxalQHgN0XUSRxS4seK144 Password: S4seK144
Identity added: /tmp/id_ed25519-K144 (Password: S4seK144)
-rw------- 1 user wheel 464 Jan 25 22:36 id_ed25519-Bhxt
-rw-r--r-- 1 user wheel 100 Jan 25 22:36 id_ed25519-Bhxt.pub
-rw------- 1 user wheel 464 Jan 25 22:30 id_ed25519-GCow
-rw-r--r-- 1 user wheel 100 Jan 25 22:30 id_ed25519-GCow.pub
-rw------- 1 user wheel 464 Jan 25 22:36 id_ed25519-K144
-rw-r--r-- 1 user wheel 100 Jan 25 22:36 id_ed25519-K144.pub
sha256: 541867de7da5d482614e872eaf47c51578347c8ff3c2df980914795eb4515f61
in addition to [https://blog.stoege.net/categories/vault/](this Blog Entry), here some instructions for OpenBSD.
https://developer.hashicorp.com/vault/docs/get-started/developer-qs
all the Steps must be run as root (or with doas)
pkg_add vault
Backup the prev. Config before …
I do …!
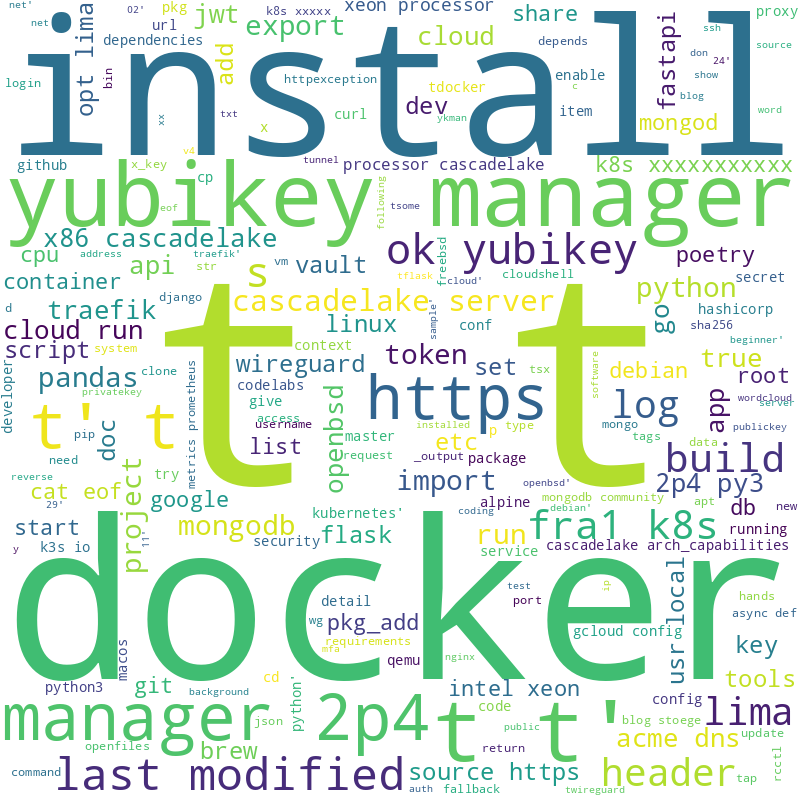
following a litte Script which Parse a Website and build a appropriate Word Cloud
mkdir ~/mywordcloud; cd ~/mywordcloud
cat <<'EOF' > main.py
import fire
import matplotlib.pyplot as plt
import pandas as pd
import re
import requests
from bs4 import BeautifulSoup
from wordcloud import STOPWORDS, WordCloud
def gen_cloud_tag(url: str = "https://blog.stoege.net"):
# add https
if not url.startswith("https://"):
url = "https://" + url
# get Webpage
response = requests.get(url, timeout=5, allow_redirects=True)
soup = BeautifulSoup(response.text, "html.parser")
words = soup.get_text()
# split with multiple delimiters
words = re.split(r"[\n\r]", words)
# build Dataframe
df = pd.DataFrame(words)
# Stop Words
comment_words = ""
stopwords = set(STOPWORDS)
# iterate
for val in df.values:
# typecaste each val to string
val = str(val)
# split the value
tokens = val.split()
# Converts each token into lowercase
for i in range(len(tokens)):
tokens[i] = tokens[i].lower()
comment_words += " ".join(tokens) + " "
# Build Wordcloud
wordcloud = WordCloud(
width=800,
height=800,
background_color="white",
stopwords=stopwords,
min_font_size=10,
).generate(comment_words)
# Build Image
plt.figure(figsize=(8, 8), facecolor=None)
plt.imshow(wordcloud)
plt.axis("off")
plt.tight_layout(pad=0)
# show Image
plt.show()
if __name__ == "__main__":
fire.Fire(gen_cloud_tag)
EOF
you need a few python libraries. use some virtual env like venv, poetry or whatever your want
buy a Key and give try …
pkg_add yubikey-manager-3.1.2p4
pkg_add yubikey-manager-3.1.2p4
quirks-6.42 signed on 2023-01-08T01:39:04Z
yubikey-manager-3.1.2p4:py3-click-7.1.2: ok
yubikey-manager-3.1.2p4:py3-pyusb-1.0.2p5: ok
yubikey-manager-3.1.2p4:pcsc-lite-1.9.8: ok
yubikey-manager-3.1.2p4:py3-cparser-2.19p2: ok
yubikey-manager-3.1.2p4:py3-cffi-1.15.1: ok
yubikey-manager-3.1.2p4:py3-cryptography-38.0.0p0: ok
yubikey-manager-3.1.2p4:py3-pyscard-2.0.3: ok
yubikey-manager-3.1.2p4:py3-openssl-22.0.0: ok
yubikey-manager-3.1.2p4:libyubikey-1.13p4: ok
yubikey-manager-3.1.2p4:json-c-0.16: ok
yubikey-manager-3.1.2p4:ykpers-1.20.0p2: ok
yubikey-manager-3.1.2p4: ok
The following new rcscripts were installed: /etc/rc.d/pcscd
See rcctl(8) for details.
--- +yubikey-manager-3.1.2p4 -------------------
NOTE: yubikey-manager (ykman) is only partially functional on OpenBSD.
Most of the "ykman fido xxx" commands (pin-setting and others) stall.
rcctl enable pcscd
rcctl start pcscd
you have to Attack your Yubikey via USB Port … … and ask dmesg about the latest news ;)
docker run -d mongo
brew install mongodb-community
To start mongodb/brew/mongodb-community now and restart at login:
brew services start mongodb/brew/mongodb-community
Or, if you don’t want/need a background service you can just run:
mongod --config /usr/local/etc/mongod.conf
pkg_add mongodb--%44 mongo-tools--
cat <<'EOF'>> /etc/login.conf
mongod:\
:openfiles-cur=1024:\
:openfiles-max=2048:\
:tc=daemon:
EOF
cap_mkdb /etc/login.conf
-> needs reboot …
rcctl enable mongod
rcctl start mongod
mongo
show dbs
> show dbs
admin 0.000GB
config 0.000GB
local 0.000GB
cat /etc/mongodb.conf
Yesterday, the 53th Relase of OpenBSD got publised, the [Version 7.2)(https://www.openbsd.org/72.html). I’ll upgrade my boxes as usual with the following Script. The most obvious change is the Performance improvement for the Package Mangager, but there is always so more see undeadly
As usual, follow to official Upgrade Guide. You can Upgrade with an USB Stick, ISO Image, PXE Boot or inline (from a running system).
As with other Versions, i have my own upgrade Script for upgrading all my boxes. Use it at your own risk and test it somewhere before you do this on your productive environment.
i like and widely use wireguard for my infrastructure. i’m also aware of it’s limitation and i know the tailscale project but never gave try. recently, i stumbled upon the headscale project, an opensource alternative to for the (closed) tailscale server. perfect, let’s give a try!
and, of course, i’m gooing to implement this with OpenBSD, what else ;)
this is working on OpenBSD 7.1, and also on the upcomming Version 7.2
i don’t like ssh & password authentication. but sometime, specially during setup or recovery, it’s need and make sense. thought i’ll protect some boxes with otp. here a few notes and instrucations
git clone https://github.com/reyk/login_otp
cd login_otp
make obj
make all
doas make install
doas otp -i
otp -g
Name: stoege
Key: xxxx xxxx xxxx xxxx xxxx xxxx xx
URL: otpauth://totp/stoege?secret=xxxxxxxxxxxxxxxxxxxxxxxxxx&issuer=&algorithm=SHA1&digits=6&period=30
echo "otpauth://totp/stoege?secret=xxxxxxxxxxxxxxxxxxxxxxxxxx&issuer=&algorithm=SHA1&digits=6&period=30" |qrencode -t ansiutf8
and scan the code with the google authenticator (or similar app)